Strengthening Blockchain Security: Countering 51% Attacks Using Dynamic Miner Reputation and Weighted Block Acceptance (DRW-BA)
DOI:
https://doi.org/10.70162/smrj/2025/v3/i1/v3i1s01Keywords:
Blockchain Security, 51% Attack, Proof of Work, Miner Reputation, Consensus Mechanism, Anomaly Detection, Smart Contracts, DecentralizationAbstract
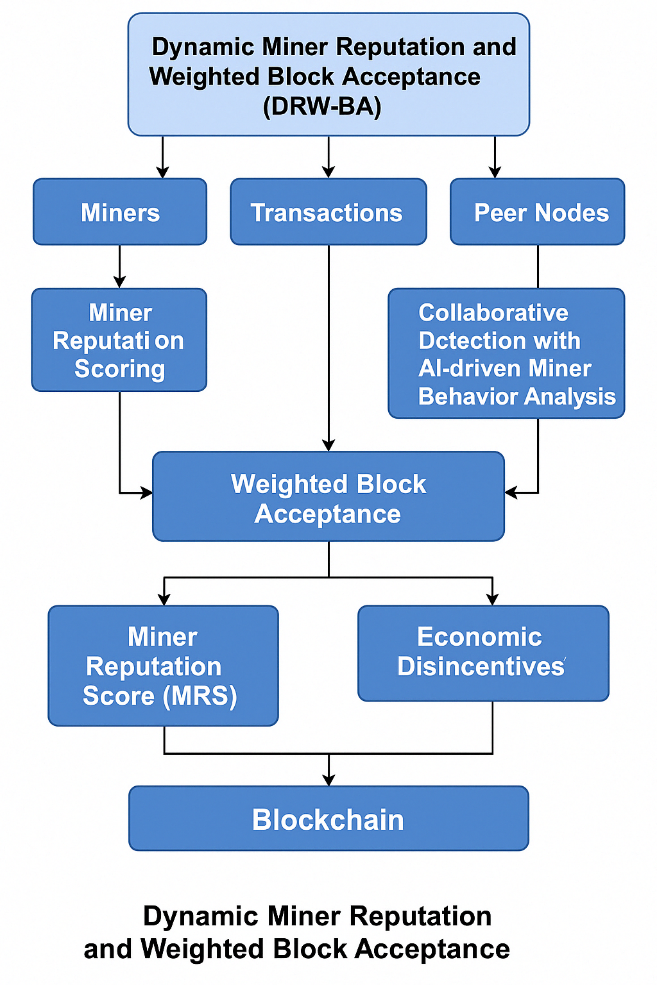
The resilience of blockchain networks—particularly those built on Proof-of-Work (PoW)—is critically threatened by 51% attacks, where a single entity or a colluding group gains majority control of mining power to manipulate transaction histories and conduct double-spending. Existing countermeasures, such as static block limits or heuristic detection techniques, often fail to address dynamic miner behavior or lack integration with real-time consensus mechanisms. This study proposes Dynamic Miner Reputation and Weighted Block Acceptance (DRW-BA), a behavior-aware defense framework designed to proactively detect and mitigate 51% attacks in PoW-based blockchain systems. The model employs a Temporal Convolutional Network (TCN) enhanced with an attention mechanism to classify miner activity (honest, bursty, colluding) based on features like Inter-Block Interval (IBI), validation frequency, and reputation drift. Miner Reputation Scores (MRS) are updated in real-time and influence a weighted consensus process that governs block acceptance. Smart contracts enforce participation limits and penalize anomalous behavior. Extensive simulations on a private Ethereum testnet demonstrate that DRW-BA achieves a macro F1-score of 0.94, an AUC-ROC of 0.96 for collusion detection, and reduces the 51% attack success probability to 7.3%, outperforming Standard PoW (78.4%) and CBL-PoW (26.7%). The model maintains an inference latency under 25 ms with less than 10.3% computational overhead. DRW-BA advances blockchain security by unifying miner behavior modeling, explainable deep learning, and smart contract enforcement into a scalable and deployable framework. Its real-time adaptability and protocol compatibility make it suitable for securing both existing and next-generation decentralized networks
Downloads
Published
Issue
Section
License

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License. You are free to share and adapt the material, but only for non-commercial purposes. You must give appropriate credit to the author(s).




